Pagoda Blog

What Is Two-Factor Authentication and Why You Need It
March 21, 2019
|
|
When it comes to security, a strong password is a good first step. But if that’s the only step you have to take to gain access to your accounts, you have a gaping hole in your defenses. Two-factor or multi-factor authentication fills in this hole with an additional barrier to entry in the form of identifying information. You may already use two-factor authentication (also referred to as two-factor verification) for some of your social media accounts or for an account that contains highly sensitive information, like your bank account. Most online platforms now offer this additional form of security and you should take advantage of it whenever possible.
Let’s look at what exactly two-factor authentication is and how it works.
What is two-factor authentication?Two-factor authentication (or 2FA) is a type of multi-factor authentication. Basically two-factor authentication requires two pieces of information to identify you and log you into an account. This information is most commonly something you know (like your password) and something you have (like your phone, fingerprints, or something called a token). Multi-factor authentication simply requires two or more factors before granting access. For most businesses, two-factor authentication provides adequate protection and is less cumbersome than requiring that third step before login.
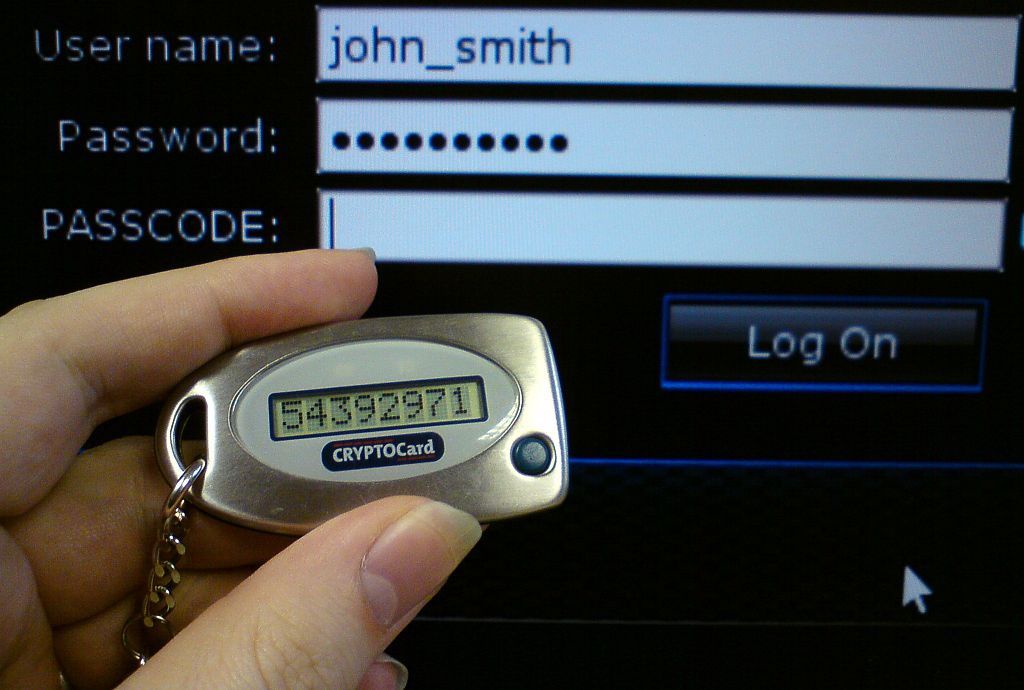
Here’s what 2FA looks like:
When you log into an account using two-factor authentication, you’re first asked for your username and password. If you correctly enter that information, you’re then prompted to enter another piece of information before gaining access. This information can be in the form of an access code (often texted to your mobile device, also known as SMS authentication, or provided through an app), a fingerprint scan or facial recognition, or a physical device called a token or security key that is inserted into your computer. For most applications, you can adjust your settings so that you don’t have to always take this extra step for recognized devices, like your home or work computer.
If you’ve ever used an ATM, you’ve experienced two-factor authentication. The ATM requires you to provide two pieces of identifying information before you can access funds: your physical debit card and your PIN.
Why 2FA is important2FA is necessary because it adds an extra layer of security between your data and potential hackers. Even if a hacker were to gain access to your password (or your debit card), they would still need another identifying piece of information to gain access to the information in your account. While it’s not entirely secure, it makes it a lot harder because they also need to have access to your mobile device, token, or 2FA app. (See the difference between SMS, token-based, and app-based authentication below.)
Example 2FA scenarios Consider the following scenarios where 2FA works to prevent an unauthorized party from gaining access to one of your accounts:
In all of these scenarios, two-factor authentication would prevent the unauthorized party from gaining access to your data because they would need a second piece of identifying information. It’s important to note, however, that in the above scenarios, the unauthorized party is always trying to gain access through an unrecognized device. Typically, for convenience, people choose to set their personal and work devices as trusted, forgoing the extra step of 2FA. Unless you share a computer at your place of work or you have frequent visitors coming and going that you believe could pose a threat, it’s probably safe to turn off the 2FA requirement on your work devices. You can always choose to still require 2FA for extra-sensitive accounts, like your company’s bank account.
SMS, token-based, or app-based two factor-authentication?Most of us are familiar with SMS-based 2FA. You enter your password to an account and then a special, one-time use code is sent to your mobile device via text. It’s often viewed as the most convenient since we almost always have our cell phone on hand. The downside is that it’s relatively easy for a hacker to gain access to your mobile phone, even without stealing the phone itself.
SMS 2FA It turns out, security weaknesses in the cell network itself allow motivated individuals to intercept text messages. This means that a hacker doesn’t need your passcode or the physical phone to read all your texts, including those with sensitive access codes. There are also expensive spyware apps that allow you to gain remote access to any mobile device. The other common way hackers gain access to your phone is through a SIM swap—when your number is moved to a new SIM card. To do this, someone simply needs your name and another personal piece of information like your social security number allowing them to call your carrier and impersonate you. It’s important to note that even though SMS 2FA is viewed as the least secure option, it’s still more secure than not using 2FA at all.
Token-based 2FA
Another more secure option is token-based 2FA. This form of two-factor authentication doesn’t rely on text messages but does require you to carry a small device. This device works two ways. One form of token, also called a security key or dongle, is inserted directly into your computer when you’re prompted for that second level of verification. It then transfers the one-time use passcode to that account. Some security keys are wireless and don’t require you to plug the device into the computer. Another type of token has a small screen that generates a new access code that you then manually type into your computer. The biggest flaw in this form of 2FA is that if you lose your token, you probably won’t realize it until the next time you login to your account. By this time, you may have already been hacked.
App-based 2FA The last option is through an app. 2FA apps are a popular choice because they work without an internet connection or cell service and are more secure than SMS-based 2FA. When you first download the app, you manually link it to all of your accounts. The app then displays a constantly rotating set of codes that can be used with those connected accounts. The main flaw of these apps is that the codes are all based on a secret key that you create during the initial set-up. Should someone gain access to this key, they could also gain access to your access codes.
Any 2FA is better than no 2FARemember, it’s impossible to secure your data 100 percent from hackers, but you can take steps to minimize the vulnerabilities and reduce the risk of someone gaining access to your accounts. If you’re currently using some form of two-factor authentication, your information is significantly safer than it would be with the basic protection of just a username and password. If you have questions about setting up 2FA for your accounts, reach out for a free consultation and we’ll walk you through the best security options for your business.
Related posts:
WordPress Security Tips to Protect Your Website From Hackers What To Do If You Receive Blackmail in Your Inbox How to Secure Your Social Media Accounts New Password Guidelines Call for Simple, Memorable Phrases
Want to get more posts like these once a month in your inbox? Sign up for the Pagoda newsletter and learn how to protect and grow your business with monthly IT tips from our experts.
Want IT to serve you better?
About Pagoda Technologies IT services Based in Santa Cruz, California, Pagoda Technologies provides trusted IT support to businesses and IT departments throughout Silicon Valley, the San Francisco Bay Area and across the globe. To learn how Pagoda Technologies can help your business, email us at support@pagoda-tech.com to schedule a complimentary IT consultation.
|
Return to Pagoda Blog Main Page |